SharePoint Dorks: Getting Juicy info in corporate Intranets

SharePoint Dorks: Getting Juicy info in corporate Intranets
In this article, we’ll explain how SharePoint can be used to find usernames, passwords, personal information, and other juicy data. To do that we’ll just transpose the concept of Google Hacking/Google Dorks to an intranet file sharing solution, such as SharePoint, Microsoft’s solution.
First, let’s start with the concept of Google Dorks.
So what are Google Dorks?
During the first steps of hacking process, the main goal is to gather as much as information as possible of the target. A well known hacking technique, Google Dorks uses Google Search to find juicy information on the Internet by performing very specific queries that use the google search advanced operators.

For example, you can search for login pages, directory listing, users, passwords, configuration files, database files etc.
-
intitle:"login": In the title of the page appears login. This is useful to find login pages and try brute force or other tactics to get into. -
intitle:"index of /" intext:".db: pages whose title includes “index of /” - a text that appears in the title of HTTP servers such as Apache when they list a folder and in which contents the text “.db” appears - which is the extension of some database files. -
inurl:.com index of movies: .com sites that include the text index of movies. Useful to find pages that have movies.
I won’t enter more in detail of the syntax or what else can be found using this technique, but if you are interested, here you have an article that expands in Google Dorks.
Also, the guys of Offensive Security have created a database with lots of Google Dorks
For the purposes of this article, the only thing you need to know is that by creating some crafted queries in a search engine you can find interesting information.
SharePoint Dorks
Ok, cool. So now that we know what are Google Dorks, what I am calling SharePoint Dorks is to apply the same concept but in SharePoint, or to any other file sharing platforms within a corporate Intranet.
The question you have to ask yourself is what search queries can I make that may expose interesting information?
By interesting information I mean queries that may return credential information of applications, social networks, admin accounts, test accounts, but also personal information such as the passport, back accounts, social security numbers, etc.
Given that the amount of documents and information indexed is limited to the corporate environment, simple queries like the ones below may pop interesting results:
passwordlogintokenoauthcredentialsinvoicepassportbank accountsocial security number,ssn- or simply a name of an employee or client
Compared with Google, SharePoint search does not offer very advanced filters or options, but you can use the SharePoint search boolean operators: AND, OR and NOT written in in capital letters. For instance:
user AND passwordlogin AND passwordinvoices AND pdf
One thing that is important to know is that when you perform a search query in SharePoint the results will only include the files you have access to including sites you have access to, and your own OneDrive. Getting those results does not mean that everyone in the organization will have access to them.
Another, notable difference with Google Dorks is that to perform a search, first you need an account on the particular SharePoint.
Why should you care?
The main reason for a regular user to be concerned about this is that some personal information may be publicly available to all your colleagues. This may include your passport, your salary, your home address, personal number, or, if you are a contractor or individual contractor, your invoices.
As I mentioned earlier, SharePoint only returns files you have permission to access to to. So, maybe even if it throws some worrying results, your information may not be disclosed to the whole organization. To validate who has access to the file
- Access the Sharepoint Site where the file is located
- And at the top right corner click on the cog icon.
- Click on Site permissions

- Expand the options to see the groups and people that are assigned to on each level.

If you see a group that says “All Staff”, “Everyone” or something like that… yes, that info is shared with the whole organization.
Why should an organization care?
Maybe you or me - because we are “good” guys ;-] - we may not be willing to use this data even if we have access to, but there are other individuals that may not think the same way. For example:
-
Disgruntled employee. There are cases in which an employee is not happy at work or he has just been fired. So, he may want to use this information to make some harm.
-
Greedy employee. This kind of insider information can be sold on the DarkNet. For example, the people behind of REvil ransomware used to buy credentials to hack into large corporate intranets.
-
Contractors Contractors may take advantage of using financial information to increase their fees, for instance, if they find invoices.
-
Hacker to escalate privileges. If a hacker was able to get the access of an employee, he will definitely try to find credentials, or information that can be valuable.
-
Hacker to send a very targeted phishing email (aka Spear Phishing). Maybe as a mean to escalate privileges or for other purposes, such as requesting the payment of an synthetic invoice .
What may be the issues?
In the case of SharePoint, I think these are a couple of issues to look at.
-
Loose default access permissions policy on new sites within the organization. This may happen if whenever a new site is provisioned, the default policy may give read access all members of the organization to all the contents.
-
Misleading Private group access. On SharePoint Collaboration Team sites, a Private group is a group on which only the Owners can add/remove members. Public groups on the other side, allow anyone to become a member. The type of group is displayed on the top right corner within the Collaboration site.
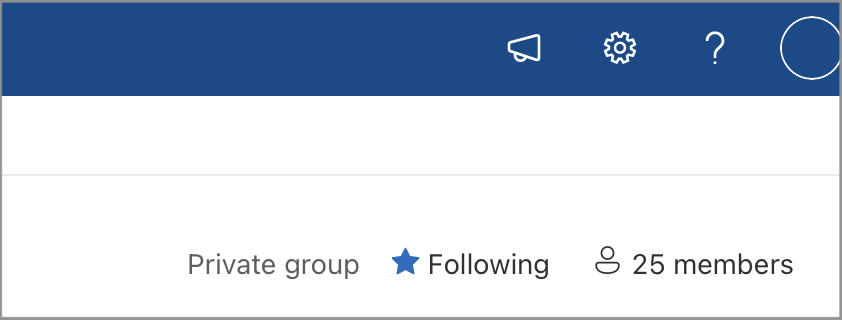
As you can see in the screenshot above, the group is Private has 25 members. This presentation may mistakenly make users to think that ONLY those 25 members have access to view the site contents and confidently share documents thinking only they have access. But that’s not true, who can view the contents is set by the users and groups that are defined within the Site Visitors access group (which can be viewed through Cog icon menu > Site Permissions > Site Visitors), and those are not reflected in the members count.
If by default, when provisioning the site, everyone in the organization is given read permissions in collaboration sites, the contents will be accessible by anyone regardless of what is displayed in the number of members.
Wrap up
Intranets and sharing documents platforms such as SharePoint, are key for efficiency and efficacy of the operations of large organizations, however, malicious players may take advantage of the search capabilities if the default permissions are not properly understood or handled, which may be tricky sometimes.
Also, note that if you try this at your workplace using your username, you may be leaving your fingerprints as search queries may be logged.
Now, your turn:
-
What other queries or useful information can be gathered? What queries may provide juicy data within an Intranet?
-
Other than SharePoint, what other Intranet solutions do you know that may be squeezed to gather interesting data?
Thanks for reading!
Disclaimer: This article is only for creating awareness of a potential issue and educational purposes.
This article was also released at: http://dev.to/merlos
 Merlos Personal Webpage
Merlos Personal Webpage